To integrate the Thereforeā¢ Server into Azure Active Directory from the backend, a custom client application needs to be registered manually in the Azure Active Directory, and the application should be configured to share 'secret' with Thereforeā¢. Application secrets can be set to "Never expire", which will assure backend access to Thereforeā¢ from the users' Azure Active Directory.
For setup:
1.Select New Registration on the Azure Active Directory.
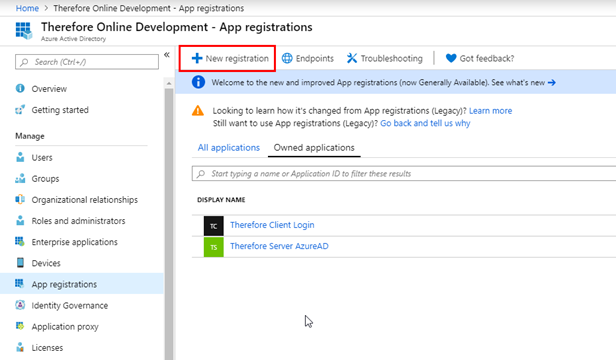
2.Create a new client application in Azure Active Directory.
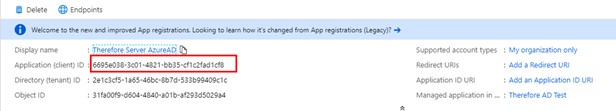

|
It is imperative to remember the clientID.
|
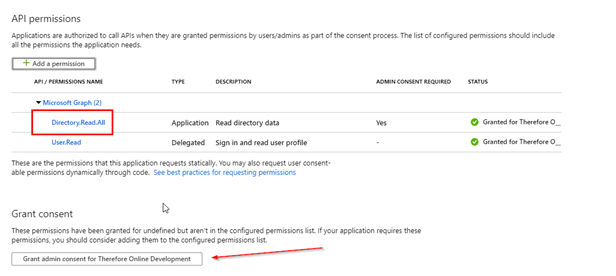
3.Request "Directory.Read.All" permissions and grant consent (by clicking the button indicated by the arrow).
4.Create a new client 'secret'; this needs to be shared with Thereforeā¢.
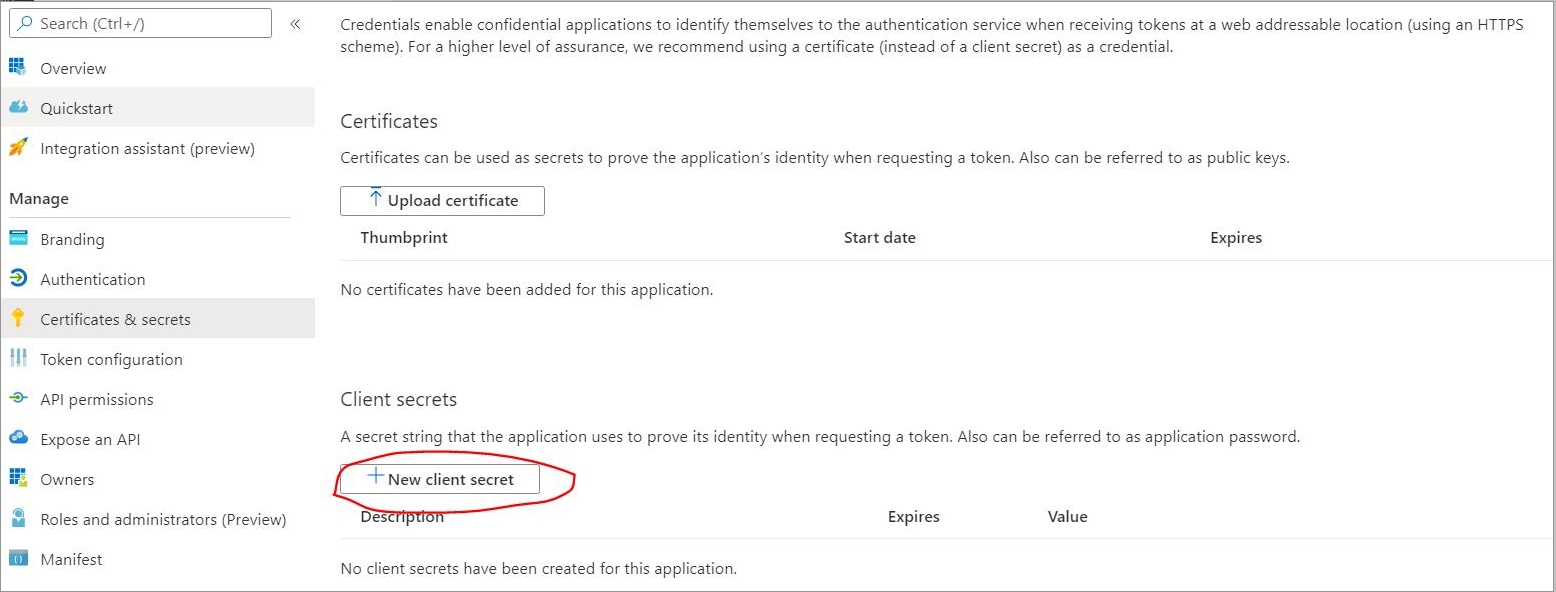
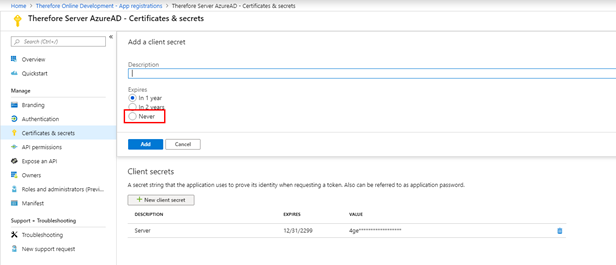

|
It is imperative to remember the client 'secret'.
|
5.These values will then need to be added to the Thereforeā¢ Azure Dialog.
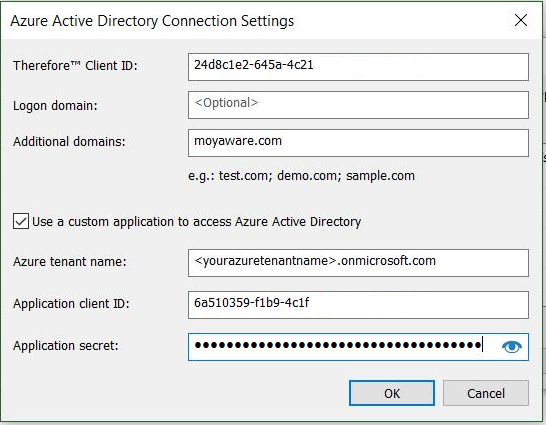
|
