
|
Configuring an OpenID Connect (OIDC) application |
Scroll |
How do I configure an OpenID Connect (OIDC) application to be used with Thereforeā¢?
1.Before OneLogin can be set up in Thereforeā¢, a new application needs to be created in the OneLogin Administration portal.
2.Add a new Application by clicking the Add App button.
3.Search for the OpenId Connect application in OneLogin and select it.
4.To clarify what this OIDC application is used for, the application can be renamed to Therefore now.

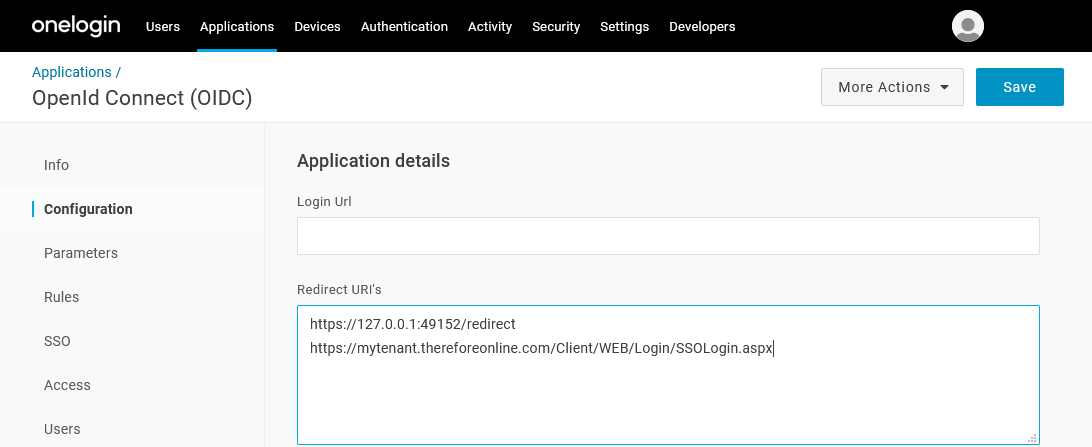
5.Optionally, images and a description can be added. Click Save to proceed. Once the application has been saved, the Configuration section allows you to specify the redirect URIs needed by Thereforeā¢. These URIs are case sensitive. Please adapt the following redirect URIs using your tenant and on-premise URL for Thereforeā¢ On-Premise (single tenant):
|
1.Thereforeā¢ Client http://127.0.0.1:64957/redirect This URI is just a placeholder as the redirect is not actually executed.
2.Thereforeā¢ Classic Web Client https://mydomain/TWA/Client/WEB/Login/SSOLogin.aspx
3.Thereforeā¢ Web Client |
6.In the Parameters section, there will already be a Groups field. However, it has to be adjusted to return roles instead of groups.
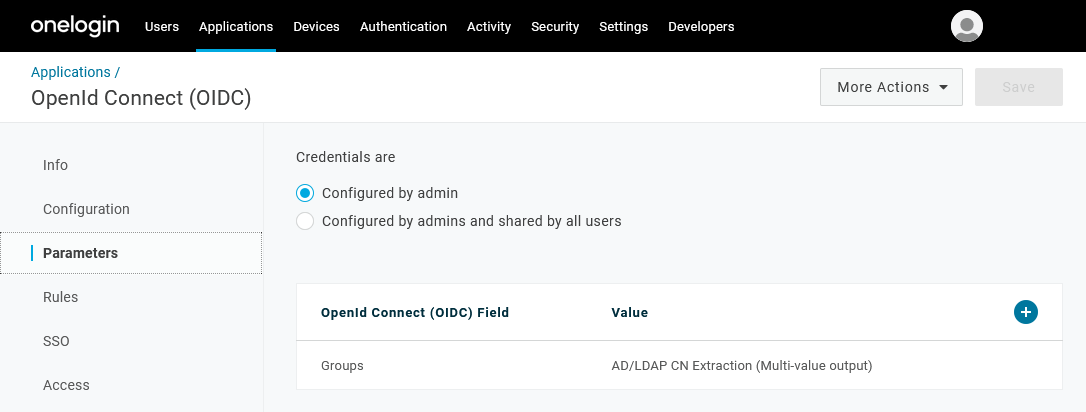
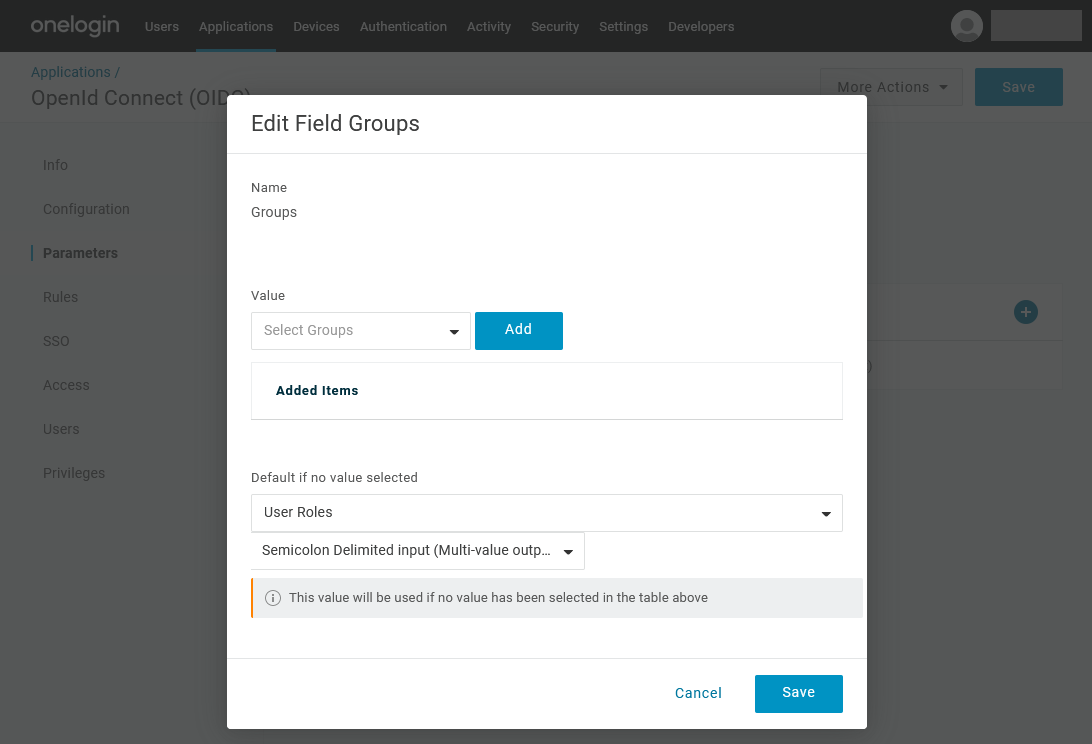
7.The default value has to be changed to User Roles with Semicolon Delimited input (Multi-value output). If this is set up correctly, Thereforeā¢ will retrieve the user roles directly from the authentication without the need for additional API requests.
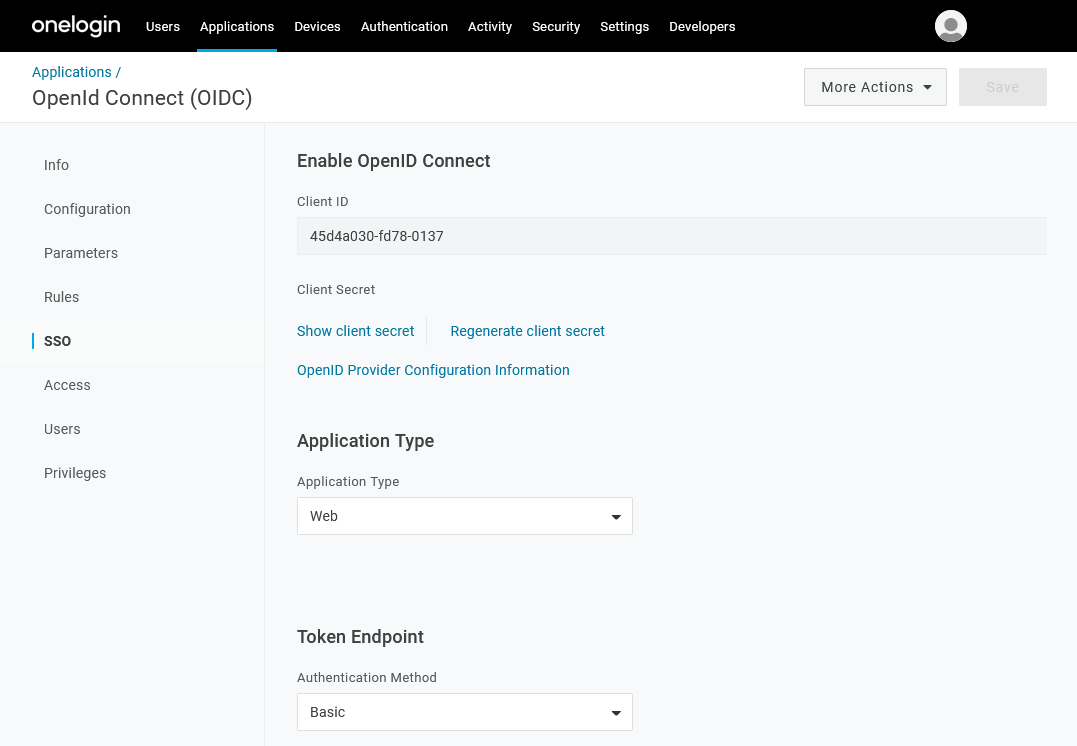
8.In the SSO section, the Application Type needs to be set to Native for Thereforeā¢ Go. Otherwise it can be left on the default setting Web. Authentication Method can be left on the default setting Basic. The Client ID is needed in the next step to configure the external directory provider in Thereforeā¢.
9.To grant users access to this new application, go to the Access section and apply a role. All users with this role will be able to use this application. Alternatively, access can also be granted for specific users but not through the Users section of the application. Instead, it needs to be granted through the Users menu entry by editing a userās applications.
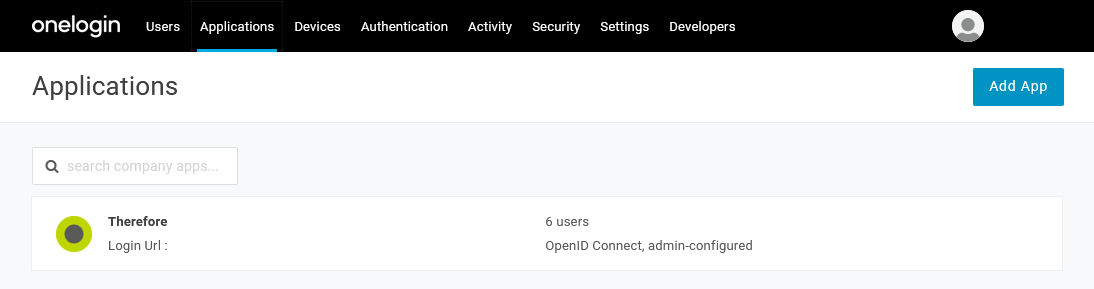
10. In the Applications menu entry, your new application will be displayed, and the amount of users that are allowed to use it will be shown.

