|
Okta |
Scroll |
How do I integrate Okta into Thereforeā¢ as a User Directory?
|
Note: •Usernames/passwords do not need to be created in Thereforeā¢ when using Okta as a cloud based user directory. Thereforeā¢ takes the users and groups defined in Okta and authenticates the user in Okta only, it then logs into Thereforeā¢ using OpenId Connect tokens. |
1.Preparation in Okta:
For the OpenId Connect token, we need to create a new Client ID in the Okta Tenant. This is a required prerequisite for this feature to work. Below are the step-by-step instructions to create such a client application for Thereforeā¢.
2.Within Okta, build your directory by creating users and user groups and assigning them accordingly.
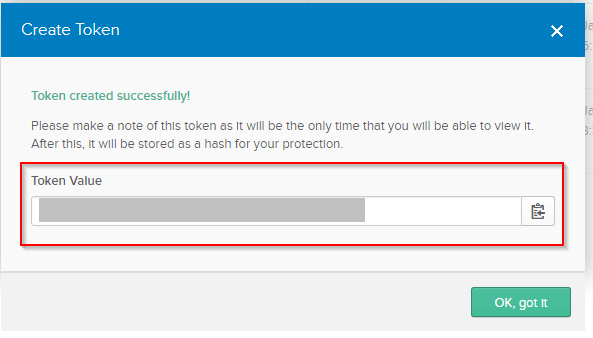
3.Create an API Token in Okta.
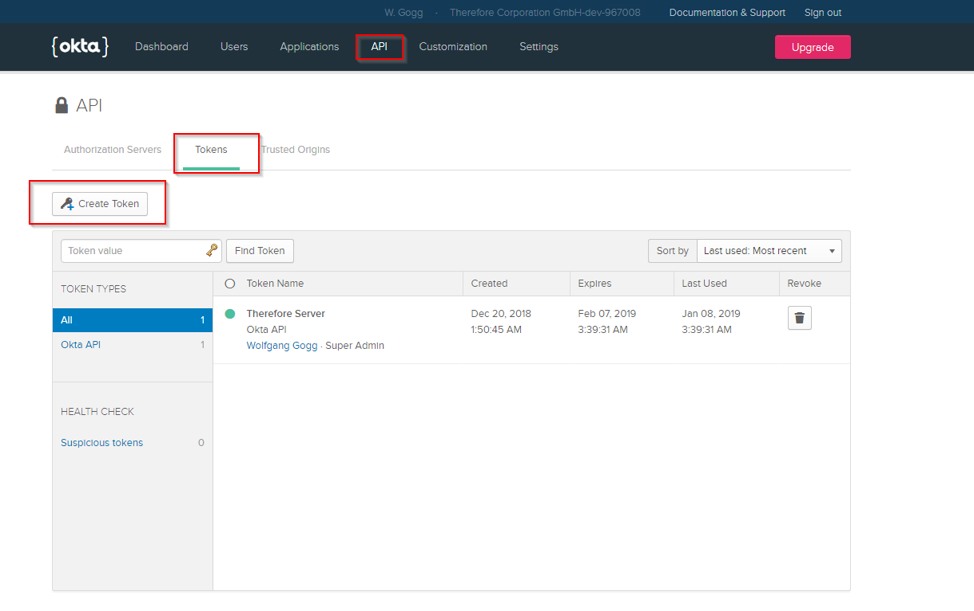
4.Name the token (e.g. āThereforeā) and click āCreate Tokenā.
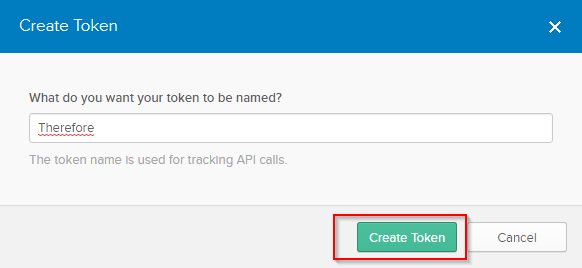
5.Copy the generated token provided in the dialog.
|
It is strongly advised to copy the token value immediately for later use, since the original token value cannot be accessed or copied again. |
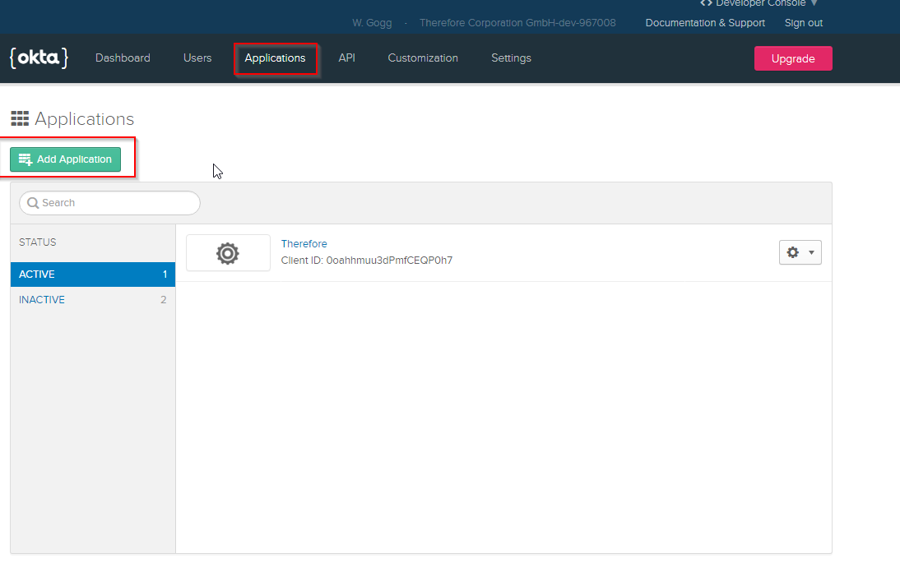
6.Create a Client Application:
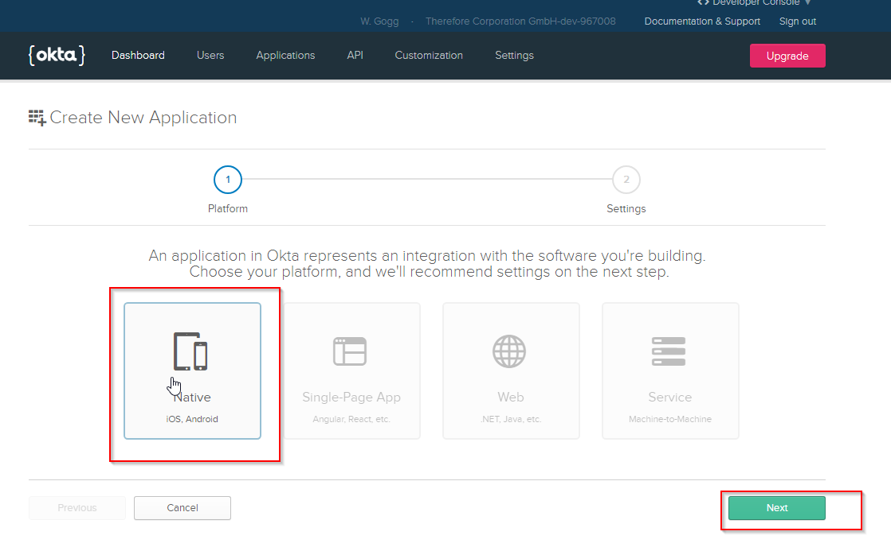
7.Configure the platform for the application.
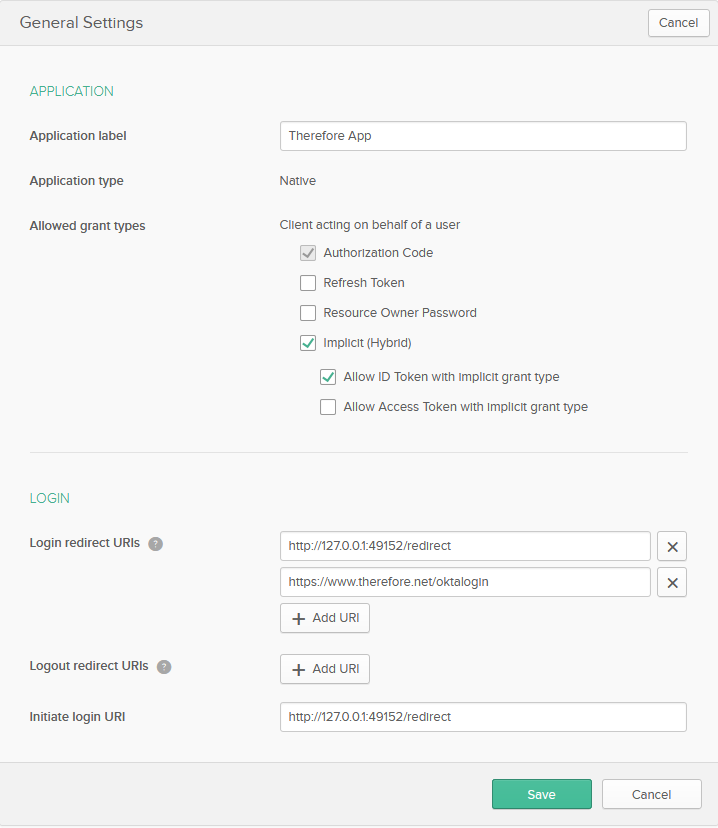
8.Configure the application settings.
|
Note: Specific redirect URIs for other Thereforeā¢ applications such as the Thereforeā¢ Go app or the Thereforeā¢ Web Client can be found here. |
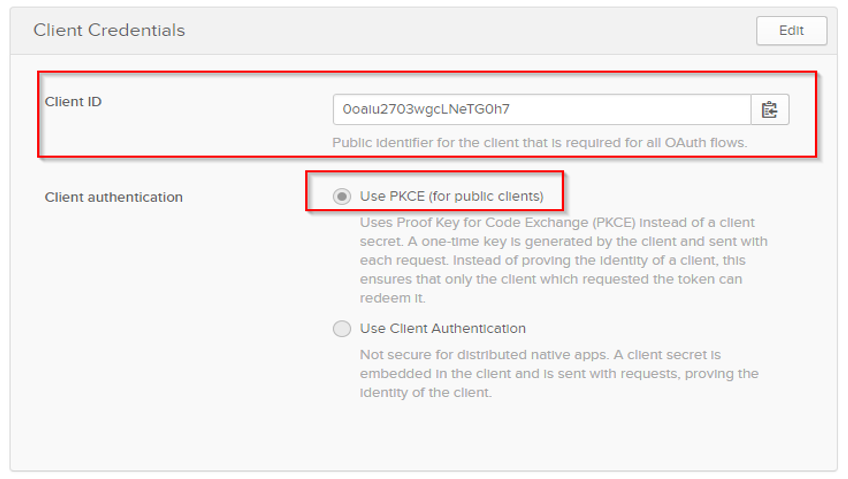
9.Copy the generated Client ID provided in the dialog and select Use PKCE under Client authentication.
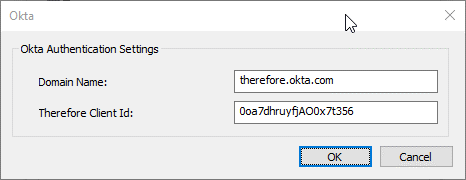
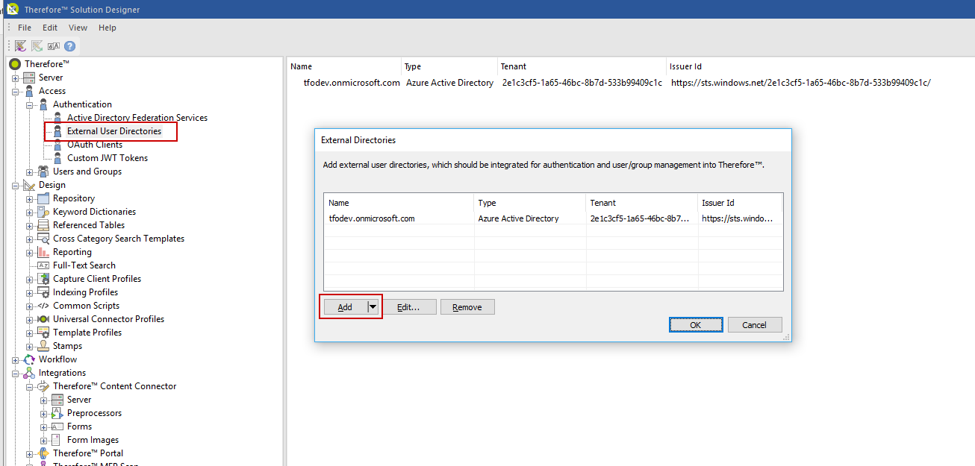
10. Establish a connection in the Thereforeā¢ Solution Designer by double-clicking on the External User Directories node. Then click Add and select the option Okta.
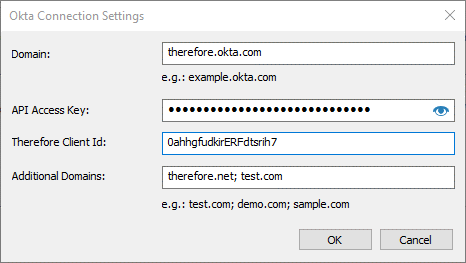
11. Enter the Okta domain name and the API Access Key, which was displayed when the client application was created. The Therefore Client Id is the ID of the client application created. Additional Domains are required if the Okta directory also contains users from other domains. For example: if the directory contains users like testuser@therefore.okta.com, and also users like test@ontherefore.com, ontherefore.com must be entered in the Additional Domains field. Click OK to establish the connection.
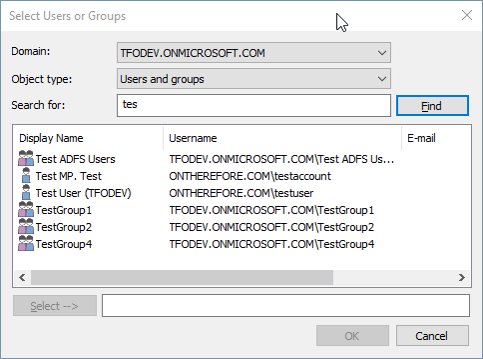
12. Once the connection has been established, the new domain can be accessed from user or group selection dialogs to select users and groups and grant the appropriate permissions.
13. When connecting to Thereforeā¢ through an installed client application, the connection settings need to be configured. For Login using, select the option for Okta, then click Settings.
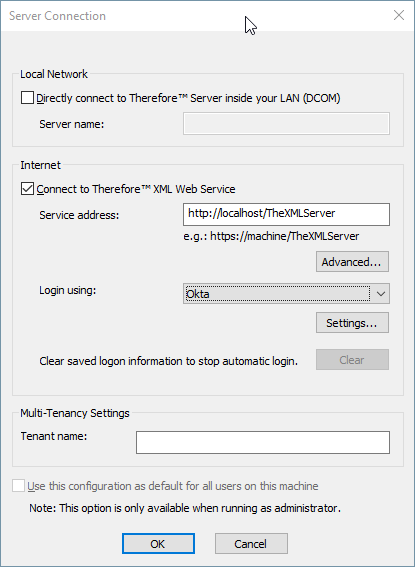
14. The Therefore Client Id must be set to the same application Id created in the preparation step, which was also added to the configuration in the Thereforeā¢ Solution Designer. The Domain name needs to be set to the corresponding Okta domain name.
|
The default client UI for logon is web-based. This is specifically required for MFA (multi-factor authentication). If no MFA is used, a user can also select to use the traditional, non-web login dialog by setting a registry key as shown below. However, this approach is not recommended.
HKEY_CURRENT_USER\Software\Therefore\Client\EnableSSOWebUi = 0
This registry value disables the web-based login dialog. If MFA is enabled, logging in will always fail in this case. |